Arm Trustzone Tutorial
Over the next few months we will be adding more developer resources and documentation for all the products and technologies that ARM provides. Credential storage enhancements in Android 43.
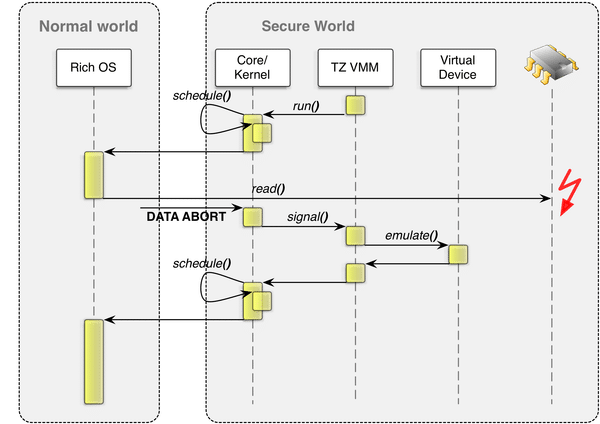
Genode An Exploration Of Arm Trustzone Technology Baylibre
EL3 on the Armv8-A Foundation Model.

Arm trustzone tutorial. Learn how the Arm TrustZone extension for the LPC5500 series works and how to start utilizing the safety measures in custom secure and non-secure applications. Open the trustzone_sam_l11_xpro_NonSecure project main_l11c in MPLAB X IDE and add the application code by following the steps below. Welcome to this tutorial series on ARM assembly basics.
This is the preparation for the followup tutorial series on ARM exploit development. 1 Under the main_l11c file in function main notice the call to the SYS_Initialize function. Investigating ARM Cortex M33 core with TrustZone Trusted Execution Environment tutorial Posted on October 21 2019 by mark embeddedpro When we are learning about TrustZone it does not take long to recognise that it is the security attributes for memory that define memory regions to be Secure Non-Secure or Non-Secure Callable.
EL is short for Exception Level. Persistent storage on Normal World. This tutorial shows you how to create an Arm TrustZone feature application on SAM L11 microcontroller MCU using MPLAB Harmony v3 software framework.
Arm TrustZone Getting Started Application on SAM L11 MCUs. Meet the Experts - Arm TrustZone - understanding system security. ARM recently announced the first two processors using the ARMv8-M architecture ARM Cortex-M23 and Cortex-M33.
ARM with TrustZone. The purpose of this lab is to introduce you to the NXP Cortex-M33 processor family using the ARM Keil MDK toolkit featuring the μVision IDE. Arm TrustZone technology provides system-wide hardware isolation for trusted software.
At the end of. Investigating ARM Cortex M33 core with TrustZone In-System Programming Tutorial Posted on November 4 2019 by mark embeddedpro This week Im back to the normal Tutorial format with a look at the In-System Programming feature in the boot ROM of the LPC55S69. ARMs developer website includes documentation tutorials support resources and more.
Then we will review how TrustZone is implemented in the hardware and software of ARM products. LibQSEEcomAPIso Selected devices Android 43 Nexus 4 Nexus 7 Keymaster operations GENERATE_KEYPAIR IMPORT_KEYPAIR SIGN_DATA VERIFY_DATA. In this paper we will discuss details of different ARM architectures that support TrustZone technology.
Arm TrustZone is an embedded security technology that starts at the hardware level by creating two. ARM TrustZone for ARMv8-M adds security featur. It enables multiple software security domains that restrict access to secure memory and IO to trusted software only.
Cortex-based cores are used in everything from microcontrollers MCUs to high-performance processors. EL3 for firmware which also acts as gatekeeper to the Secure world TrustZone. Before we can dive into creating ARM shellcode and build ROP chains we need to cover some ARM Assembly basics first.
The SAM L11 MCU is the implementation of the Arm TrustZone 45r for. The platform contains training modules covering a wide range of topic from AMBA bus protocols to DynamIQ and Armv8-A. Arm TrustZone is a system-wide approach to embedded security option for the ARM Cortex-based processor systems.
Keymaster Trusted app. With increasingly connected devices and the increasing sophistication of hackers many companies like NXP Semiconductors have recognized a need for countermeasures. Arm TrustZone technology is a System on Chip SoC and CPU system-wide approach to security.
ARM is widely deployed on the majority of mobile and micro-controller devices TrustZones goal is to provide security for those platforms. The Arm On Demand Online Training platform has been designed to give you access to online videos assessment and document based training when and where you want it. While this tutorial series primarily focuses on the interactions between EL1 and EL2 note that an Arm processor will always reset into the highest implemented exception level ie.
The TrustZone for Armv8-M security extension is optimized for ultra-low power embedded applications.

Investigating Arm Cortex M33 Core With Trustzone In System Programming Tutorial Mcu On Eclipse
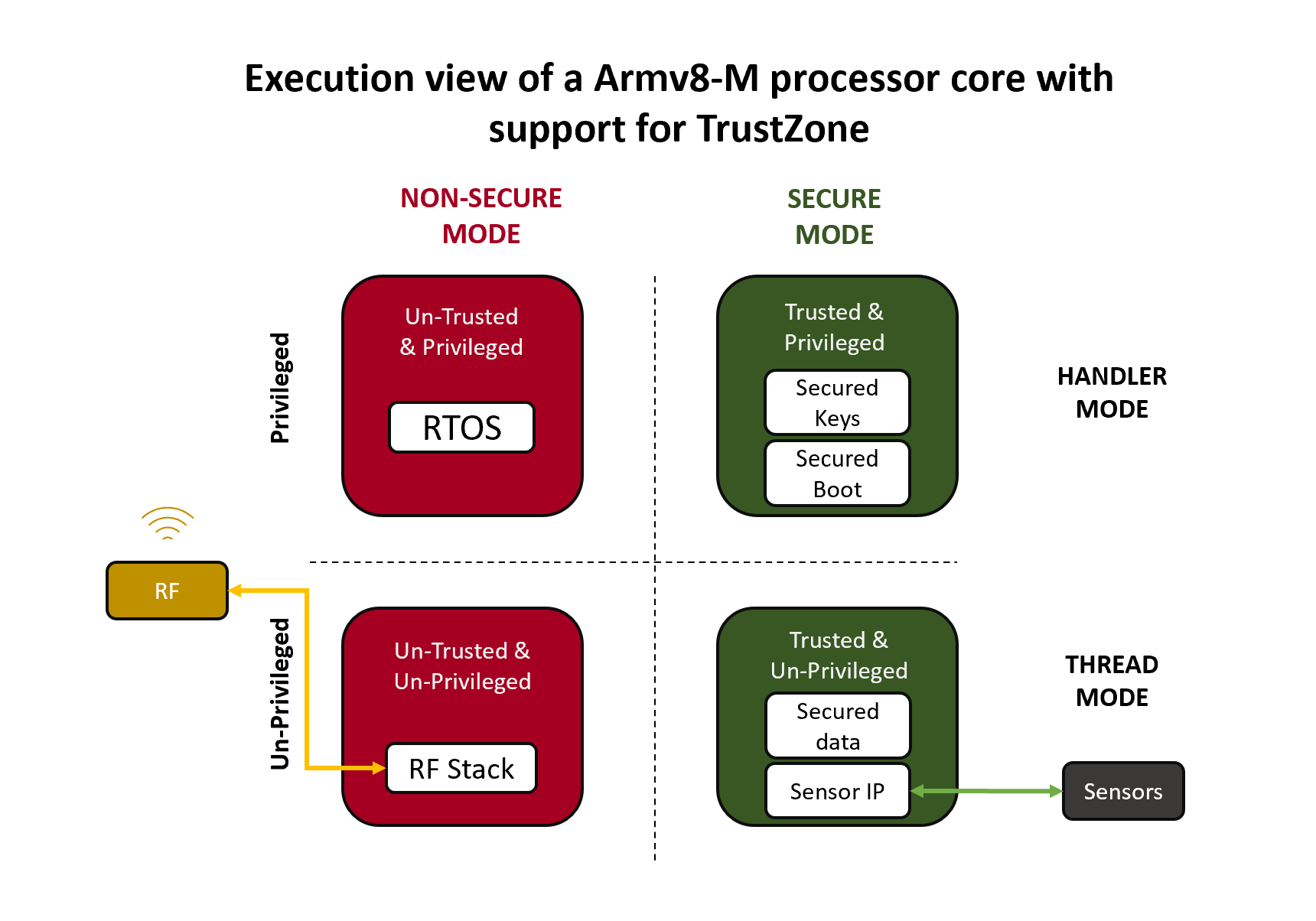
Demystifying Arm Trustzone For Microcontrollers And A Note On Rust Support
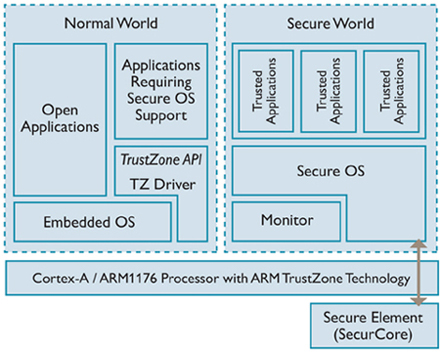
Introduction To Trusted Execution Environment Arm S Trustzone

Arm Trustzone Technology Youtube